 It’s not very often that people admit to being hacked. However, I had the shock of my life today. One of my servers had been brute-forced at the RPC level recently. The hacker came into the network at the machine level, not the domain. Even so – this was our main terminal server and it took a while to understand what was happening:
It’s not very often that people admit to being hacked. However, I had the shock of my life today. One of my servers had been brute-forced at the RPC level recently. The hacker came into the network at the machine level, not the domain. Even so – this was our main terminal server and it took a while to understand what was happening:
I had spotted a rogue Administrator session running a few times during the month and just terminated it – thinking nothing of it. I just thought my colleague had hit a few too many buttons and left it running by accident.
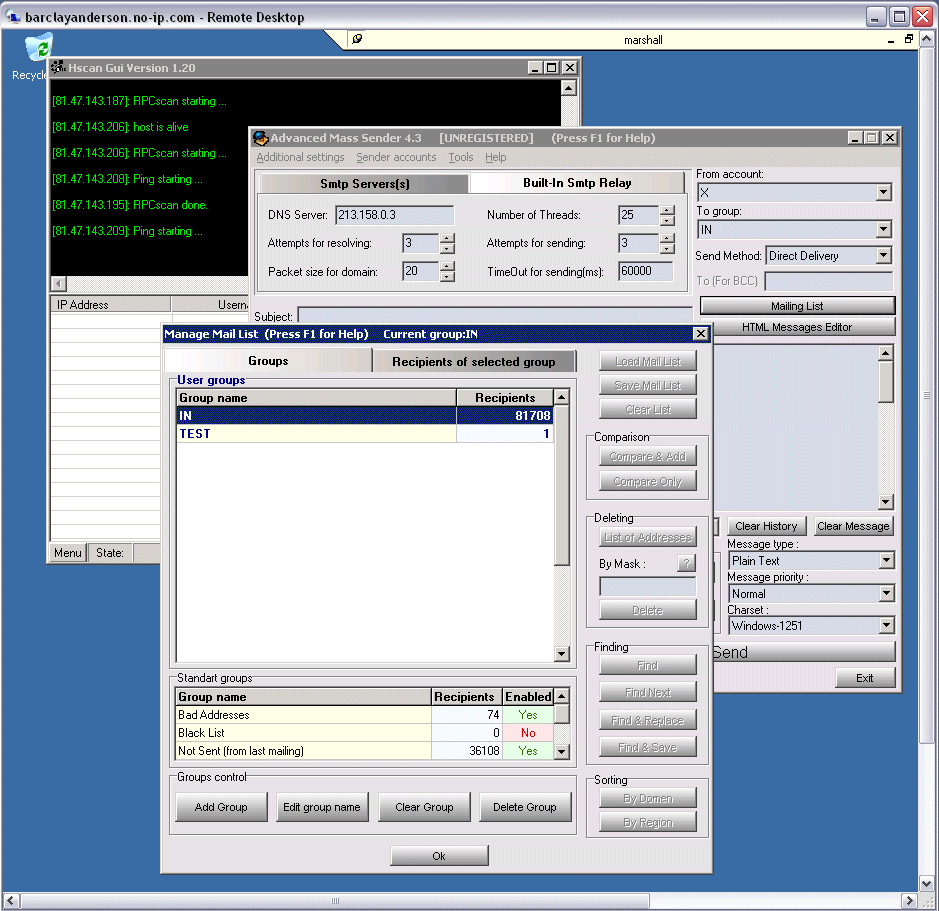
Today by chance, I found the account “active” – so I jumped in and remote controlled the session. There was a scanner running on it brute forcing loads of machines at the IP level and at the same time running a Phishing email server, sending out squillions of emails hunting down usernames and passwords for bank (click screenshot to see more).
I watched for a few seconds and then fired up Notebook and typed, “Who the fXck are you?”. Looking back, it’s a shame really I scared him. We than had a bit of a fight over the mouse! I won because I just kept clicking the desktop. Occasionally, the hacker would get the log off screen up, but I would desktop-click the session again before he could click “log off”. Finally, I managed to “disconnect” both of us and then proceeded to race up the server chain to change the domain password. Poor guy must have had a bloody heart attack. Imagine, peacfully minding your own hacking business when someone comes in and remote controls your hacked desktop!
Anyway, a few moment later, I spotted him “active” again using the session. I dived in silently, watching him check the status of his stuff and then he disconnected again. My problem was that I could not take over his session when he was disconnected because he’d changed the damned machine admin account password. I couldn’t work this out immediately though because I was trying to manage his session with the (now changed) domain password and it wouldn’t work. I just couldn’t work it out why it wouldn’t work. When I tried to remote control the session, the domain password kept failing. Grrr.
All at once, it came to me. The local machine password wasn’t at all complex. I realised that I’d been compromised at the local machine level with a dictionary attack probably over many months. It wasn’t the domain that was compromised at all. I jumped into My Computer straight into “Manage” and did an emergency password reset using the domain account to over-ridce the local account. You get warned that you’ll lose some certificates and stuff because it’s not the de rigeur method, but I wanted him out for good. Once changed, he was locked out. I put the kettle on and browsed the mess.
He’d installed a number of components including an unzipper (RAR), AMS 4.3 (Advanced Mass Sender) with 15 days to go on the free trial(!), Hscan (a scanner) and XAMPP, a small platform apache site (http://www.apachefriends.org/en/xampp.html) which was installed only as a service – that took me a while to find. It appears that the program had been fully installed and then uninstalled, leaving only the background service running. What makes matter more difficult is that many of the tools were renamed to standard Windows tools; for instance the scanner (see below) was called “taskmgr.exe”. The bottom line is that this was about to become a fully blown phishing platform whilst it looked for its next IP address – and it was about to be hidden away from me. Scary thought.
Observing the mess, I particularly liked the scanner (HScan) since I had only heard of this stuff, never played with it. You select a range of protocols and an IP address range and just set the thing off scanning for days and days. It gradually builds a report in HTML of all the IP addresses it found open with the protocols you selected. You then paste these IPs into a file and set off the dictionary hack using the known probable administrator account login. This is why its important to put a 10 minute lock-out on the account after only a few password attempts.
The “About” stuff shows:
HScan Gui Version 1.20 – HUC Network Security Scanner
Copyright (C) 2000-2003 HUC All Rights Reserved.
By uhhuhy (Mar 05,2003)Mailto: *** withheld ***
Personal-Homepage: *** withheld ***HScan is a powerful network security scanner.
Scan modules:
PORT/FTP/SSH/TELNET/SMTP/FINGER/IIS/CGI/POP
/RPC/IPC/IMAP/MSSQL/MYSQL/CISCO/PLUGIN.
Multi-threading makes HScan very fast.IP scope and host list
are both supported.
Do normal people call the police? Maybe, but I was worried about having the whole server fleet trucked to Police HQ as evidence and being left with nothing to run the business on. Interesting debate.
It’s unlikely you will come face to face with your opponent like I did, fighting over a desktop! It was scary and I nearly pulled the cat 5 cable out the wall because your brain freezes up in these situations. However, I stayed calm and I did the right thing in the end. It was a bit like being in a film at one point. Mayur was standing behind me, “General!”, he shouted (yes, he calls me General!), “you’re hands are shaking”. Damned right they were.
Morale of the story? Even though you may have strong domain passwords, check the local machine account names and passwords for complexity rules in Group Policy. Also change the administrator account name (apparently you will be forced to do this with Server 2008 – thanks Stuart for the tip – and the three pints :).
Happy New Year everyone.
Callum.
 We’re having a narrowboat built currently by Louis and Joshua narrowboats in Doncaster (USA visitors, please google “narrowboat”) and obviously I’m preparing for some /portable radio work with a small shack being built for me to house a laptop, FT1000MP and a small ACOM (this being a radio ham site, I thought I ought to put that bit in).
We’re having a narrowboat built currently by Louis and Joshua narrowboats in Doncaster (USA visitors, please google “narrowboat”) and obviously I’m preparing for some /portable radio work with a small shack being built for me to house a laptop, FT1000MP and a small ACOM (this being a radio ham site, I thought I ought to put that bit in).
 I have finally discovered a way of remembering the difference between license and licence. “Licence” is a noun and “license” is a verb. Since I refer to the noun more than the verb, I shall remember that there are no Ss in LICENCE.
I have finally discovered a way of remembering the difference between license and licence. “Licence” is a noun and “license” is a verb. Since I refer to the noun more than the verb, I shall remember that there are no Ss in LICENCE.